Dark Web Profile: DragonForce Ransomware
DragonForce Ransomware has emerged as an intriguing adversary. Known for its prominent targets and unusual ways of communication, it has quickly gained notoriety among cybersecurity experts and victims alike. This post delves into the origins, operations, and distinctive features of the DragonForce Ransomware, shedding light on the menacing threats in the digital world today.
Threat actor card for DragonForce Ransomware
Who is DragonForce Ransomware?
First identified in December 2023, DragonForce, a Ransomware-as-a-Service (RaaS) affiliate program, has been tied to high-profile attacks. It deploys two ransomware variants, tailoring attacks by modifying file extensions and terminating specific processes. Its builder enables affiliates to choose processes to halt, ensuring effective data encryption.
The group behind DragonForce, allegedly connected to the notorious LockBit ransomware gang, has demonstrated capabilities in penetrating networks and encrypting data. Their operations reflect a blend of traditional ransomware tactics and innovative(?) strategies designed to maximize financial gain.

DragonForce Ransomware’s Logo
While LockBit was dethroned as the most dangerous ransomware due to the operation of the security forces, it could be thought that hundreds of affiliates, ransomware strains, and knowledge would flow somewhere. Therefore, a case involving DragonForce also raised the possibility that it might be related to LockBit.
As Graham Cluley reported, in mid-March 2024, the government of Palau experienced a ransomware attack that incapacitated their computers. Unusually, ransom notes from two different hacking groups, LockBit and DragonForce, were discovered.
However, this indicated that they were using the leaked LockBit builder rather than having a connection with LockBit. The double ransom note can be interpreted as an error due to technical inadequacies.
Some members of the cybersecurity community have associated the ransomware with DragonForce Malaysia, a hacking group and forum based in Malaysia. However, these claims were denied on DragonForce Malaysia’s Telegram channel.
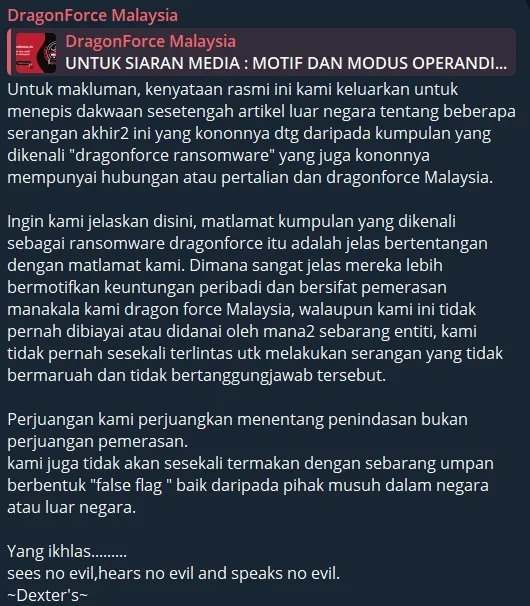
DragonForce Malaysia’s Telegram post about ransomware connection
Translated with ChatGPT: “FOR MEDIA RELEASE: MOTIVE AND MODUS OPERANDI…
For your information, we are issuing this official statement to refute claims made in some foreign articles about several recent attacks which are allegedly from a group known as “DragonForce Ransomware”, which supposedly has links or relations to DragonForce Malaysia.
We would like to clarify that the goals of the group known as DragonForce Ransomware clearly go against our own objectives. It is very clear that they are more profit-driven and act in an extortionate manner. On the other hand, DragonForce Malaysia, although we are not funded or sponsored by any entities, has never had the intention to carry out attacks that are unethical or irresponsible.
Our fight is a struggle against oppression, not a fight for extortion.
We will never fall for any bait in the form of a “false flag”, whether from domestic or foreign enemies.”

On June 26, 2024, a user named “dragonforce” promoted the DragonForce Ransomware-as-a-Service (RaaS) program on the RAMP forum. The post offered affiliates 80% of ransom payments and highlighted features like client tracking, automated file delivery, XDR/EDR bypass, encryption, SYSTEM impersonation, and full support services.
So, who exactly is DragonForce? We don’t know, maybe we should ask.
DragonForce Ransomware’s DLS, contact form
What are DragonForce Ransomware’s Techniques?
When they first emerged, DragonForce Ransomware was seen utilizing a leaked ransomware builder from the LockBit ransomware group. LockBit 3.0, also known as LockBit Black, is the third version of a notorious ransomware family. Created by the LockBit group, it was infamously leaked in September 2022 by a disgruntled developer. This leak has allowed various cybercriminal factions, including the newly emerged DragonForce ransomware group, to exploit its capabilities for launching sophisticated attacks.
The DragonForce gang aims to extort their victims, and they use a double extortion strategy, where they lock victims out of their infected machines and exfiltrate data before encrypting it. If the victims do not comply with their demands, the threat actor threatens to release the data on their DLS.
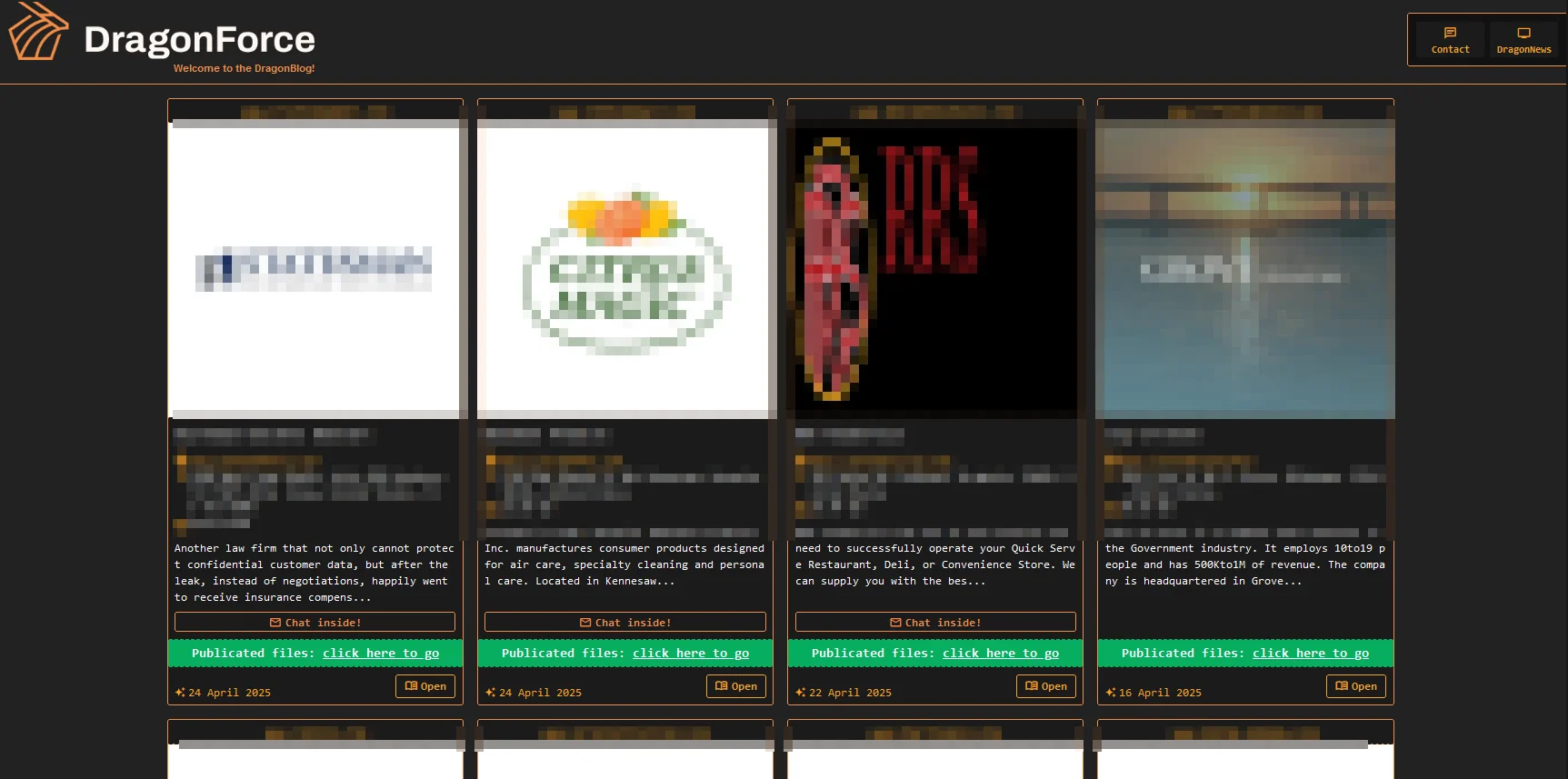
Main page of DragonForce Ransomware’s Data Leak Site (DLS)
DragonForce is a Ransomware-as-a-Service (RaaS) group. Since its public affiliate program debut in 2024, the group has grown into a sophisticated threat group with an increasing number of global targets.
Initial Access
DragonForce affiliates use multiple vectors to infiltrate target networks. These include phishing campaigns, exploiting known vulnerabilities such as Log4Shell (CVE-2021-44228), and brute-force attacks against Remote Desktop (RDP) and VPN services. In some incidents, the group has also leveraged compromised credentials to access public-facing systems directly.
Once inside a network, affiliates deploy tools like Cobalt Strike for post-exploitation, Mimikatz for credential theft, and SystemBC for persistence and command-and-control (C2) tunneling. Their initial access is often followed by lateral movement through RDP and the exploitation of internal trust relationships.
Affiliate Platform
DragonForce offers affiliates access to a dedicated panel that streamlines attack planning and ransomware deployment. Each affiliate is assigned a unique .onion address and uses their own profile to manage operations. The platform includes sections for client management, payload configuration, leak site publication, and revenue tracking.
Affiliates can generate two types of payloads:
- A LockBit 3.0-based variant, familiar to seasoned operators
- A custom DragonForce build—based on a modified ContiV3 sample—that supports advanced options like EDR/XDR bypass and system-wide encryption
These payloads are fully configurable. Operators can set the encryption scope (local or network), exclude specific files or directories, define ransom note content, and even customize encryption extensions and wallpapers. Importantly, both versions support the use of vulnerable drivers—a technique known as BYOVD (Bring Your Own Vulnerable Driver)—to kill antivirus or EDR processes silently at the kernel level.
Execution and Encryption
Once the payload is deployed, the ransomware encrypts files using AES-256, RSA, or in newer builds, ChaCha8 for faster performance. Files are appended with a “.dragonforce_encrypted” extension, and the ransomware may encrypt either the entire network or specific targeted systems.
DragonForce also employs process injection, SYSTEM impersonation, and access token manipulation to elevate privileges and maintain control. Their payloads automatically clear Windows event logs post-encryption to hinder forensic recovery and log analysis.
In one confirmed case from September 2023, DragonForce was observed moving laterally through an environment using RDP while running credential dumps and launching their payload. They used tools like ADFind to map Active Directory, SoftPerfect’s network scanner for internal reconnaissance, and SystemBC for persistence.
Extortion and Leak Site Operations
Data exfiltration is a core part of DragonForce’s double extortion scheme. Stolen data is transmitted over SFTP, WebDAV, or uploaded directly to MEGA or DragonForce’s own Dedicated Leak Site (DLS). If victims refuse to pay, the data is scheduled for publication through a “Constructor” module in the affiliate panel.
Affiliates track negotiation status and ransom demands through the platform. The panel logs victim details, ransom statuses, encryption progress, and leak timing. For high-value victims, operators often set deadlines or release partial data as leverage.
Defensive Evasion and Persistence
DragonForce incorporates advanced evasion tactics. These include:
- Clearing event logs after encryption (T1070.001)
- Creating registry keys for persistence (T1547.001)
- Installing Windows services to ensure reboot survival (T1543.003)
- Encrypting filenames and applying obfuscation to hinder reverse engineering
- Creating scheduled tasks to re-launch payloads
They also leverage Access Token Duplication to run processes under SYSTEM-level accounts, further avoiding security controls.
A Modular and Evolving Threat
DragonForce’s modular ransomware, ability to deliver both Windows and ESXi variants, and rapid onboarding of affiliates make it a scalable and dangerous operation. Its reliance on established malware frameworks like Conti and LockBit, combined with added features such as BYOVD and detailed logging, reflect the group’s technical sophistication.
This structure allows DragonForce to operate as a hybrid of a criminal enterprise and malware startup—able to serve both experienced ransomware operators and new affiliates alike. Its ongoing development and emphasis on customization make DragonForce one of the most adaptable and concerning ransomware threats today.
What are DragonForce Ransomware’s Targets?
The DragonForce ransomware group has shown a clear pattern of targeting a broad range of industries and regions. Their victim list includes organizations from both private and public sectors, with a strong focus on industrial, critical, and service-oriented entities.
Most Targeted Industries
Based on incident data, Manufacturing stands out as the most targeted industry. This includes companies producing everything from electronics and metal goods to aerospace parts and industrial equipment. The group seems to exploit the high operational disruption costs in this sector.
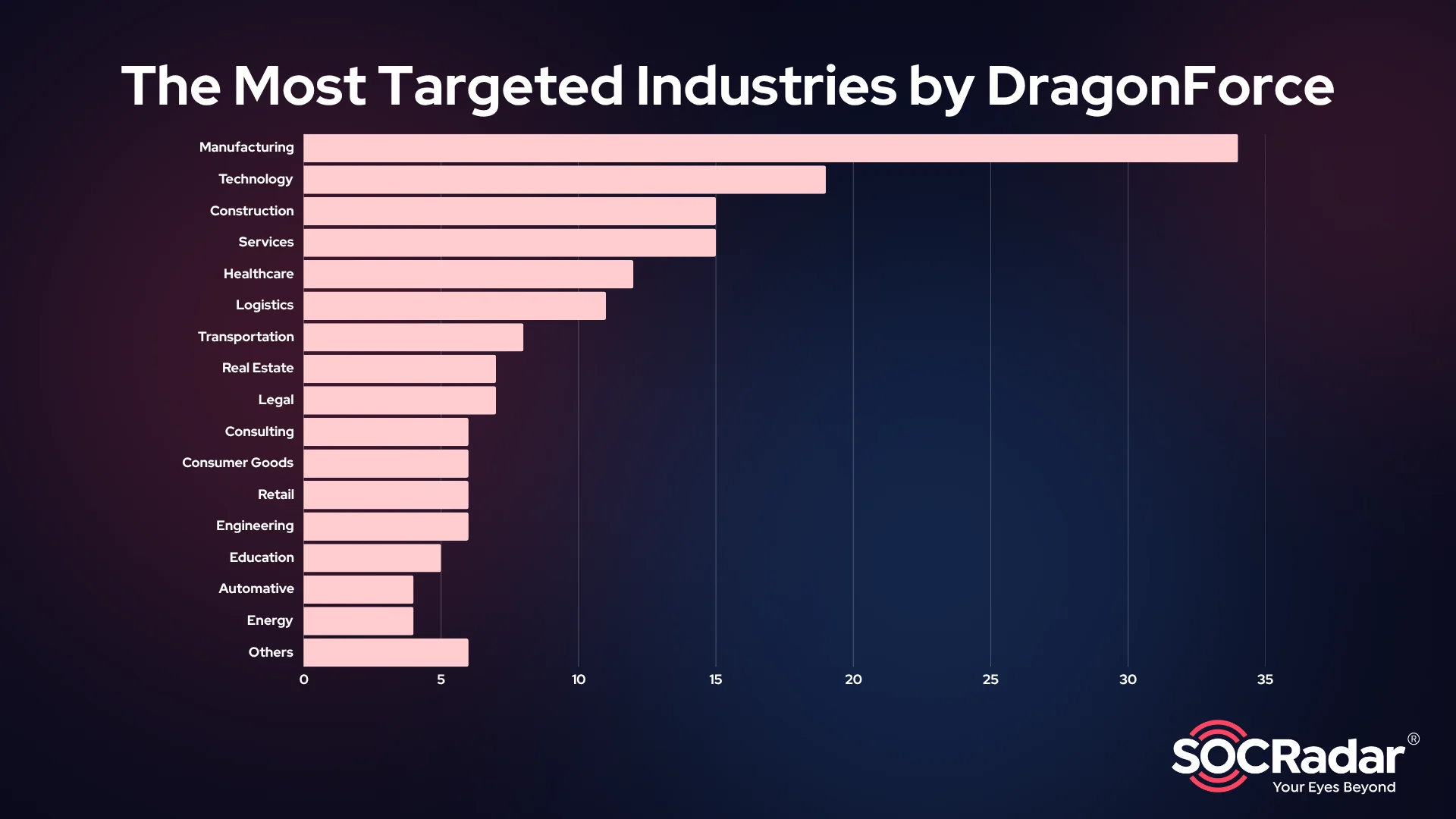
The most targeted Industries by DragonForce Ransomware
Next are Technology and Construction, each attracting high levels of attention. Technology includes IT services, software providers, and telecom companies, while construction covers infrastructure and building supply firms.
Other heavily hit industries include:
- Healthcare: hospitals, clinics, and specialty care centers
- Logistics and Transportation: supply chain, distribution, and transit firms
- Legal and Consulting: law offices and business advisory companies
- Retail and Consumer Goods: especially in e-commerce and distribution
- Public Services: such as funeral homes, religious institutions, and local government offices
This diversity suggests that DragonForce does not specialize in one vertical. Instead, they focus on targets with high data value or operational sensitivity.
Most Targeted Countries
The United States is by far the primary target, with over half of all known victims based there. This is followed by the United Kingdom, Australia, Italy, France, Germany, New Zealand, Czechia, and Canada.
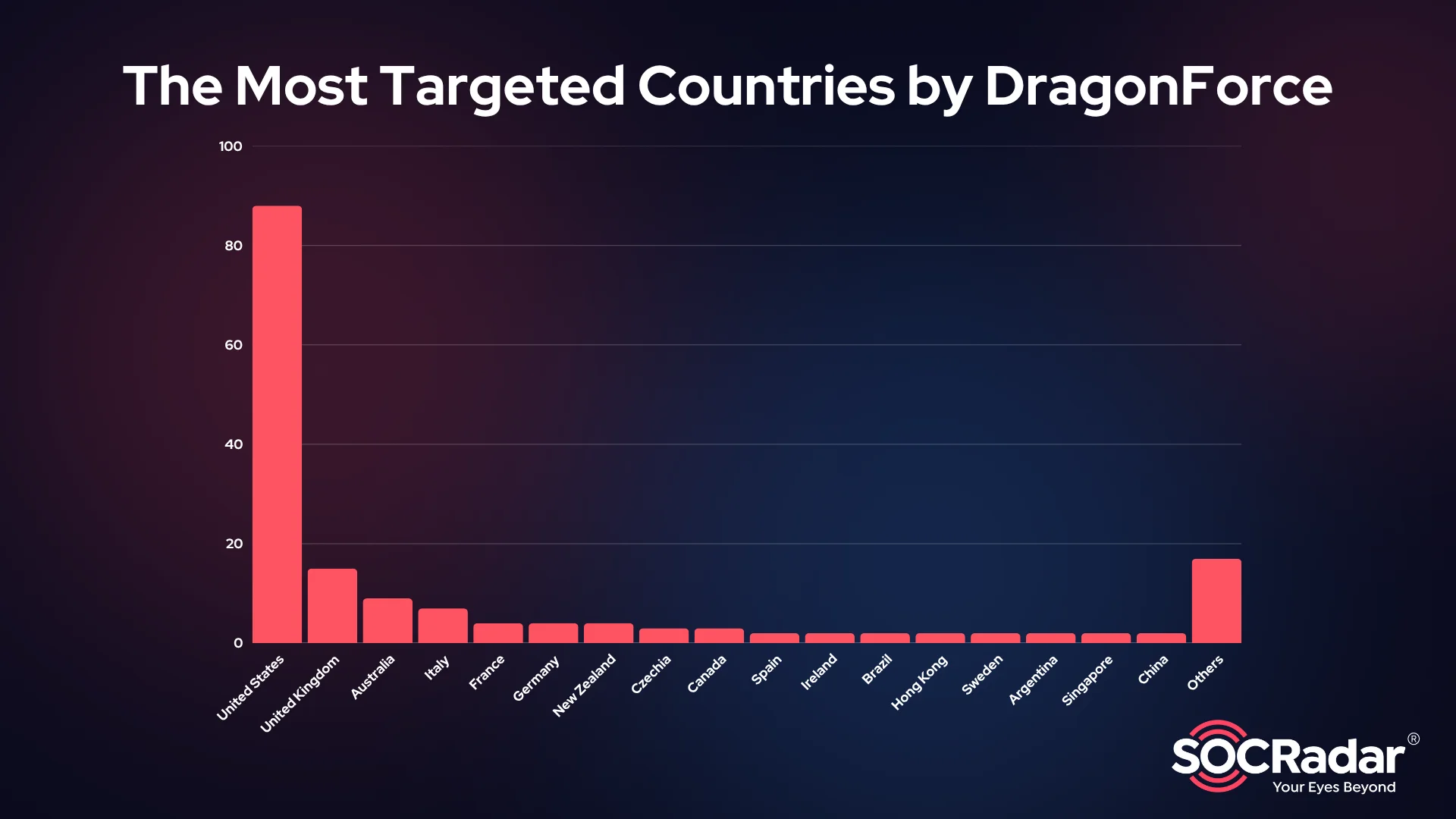
The most targeted countries by DragonForce Ransomware
The strong presence of Western countries among the victims is not surprising, as these regions tend to have more developed digital infrastructure and a higher concentration of profitable sectors like manufacturing, technology, and finance. However, the noticeable absence of targets in Russia and CIS countries is not coincidental, many ransomware groups intentionally avoid these regions, which significantly skews the overall distribution.

What are the Mitigation Tactics Against DragonForce Ransomware?
Email Security & Phishing Prevention
- Deploy advanced email filtering solutions to detect and block phishing emails and malicious attachments.
- Conduct regular phishing simulations and user awareness training to identify social engineering attempts.
Patch Management
- Apply security updates promptly, especially for critical vulnerabilities like Log4Shell (CVE-2021-44228) and others known to be exploited.
- Regularly audit software and systems to identify unpatched vulnerabilities.
Credential Protection
- Enforce strong, unique passwords with mandatory rotation policies.
- Use Multi-Factor Authentication (MFA) on all remote access points including RDP and VPN.
Remote Access Hardening
- Disable RDP if not needed; otherwise, restrict access via VPN and allow-list IPs.
- Limit access rights and enforce network segmentation for external connections.
Network Segmentation
- Isolate critical infrastructure, domain controllers, and backup servers.
- Use VLANs and firewalls to reduce lateral movement opportunities.
Endpoint Detection and Response (EDR)
- Deploy robust EDR solutions capable of detecting tools like Cobalt Strike, Mimikatz, and SystemBC.
- Regularly update detection rules to monitor for known TTPs used by DragonForce affiliates.
Behavior-Based Monitoring
- Look for unusual login patterns, excessive RDP connections, privilege escalation attempts, and suspicious scheduled tasks.
Application Whitelisting
- Restrict the execution of unknown or unauthorized software, especially in user and temp directories.
BYOVD Mitigation
- Use tools like Microsoft Defender Application Control (MDAC) to block untrusted drivers and kernel-level tampering.
- Monitor for unexpected driver installations or loading of vulnerable drivers.
Privilege Management
- Implement least privilege access to limit SYSTEM-level or administrative privileges.
- Monitor and restrict token manipulation and impersonation attempts.
Data Loss Prevention (DLP)
- Deploy DLP tools to monitor and restrict the transfer of sensitive data through SFTP, WebDAV, or cloud storage platforms.
Outbound Traffic Filtering
- Block access to known malicious IPs, Tor nodes, and leak site domains (.onion addresses).
- Use proxy or DNS filtering to prevent unauthorized outbound connections.
Backup and Recovery
- Maintain offline, immutable backups stored separately from the main network.
- Test backup restoration procedures regularly to ensure readiness after an attack.
Event Log Protection
- Monitor for sudden or unusual event log clearing activity (T1070.001).
- Forward logs to a centralized, secure SIEM for retention and analysis.
Registry and Scheduled Task Monitoring
- Track changes to startup registry keys and new task scheduler entries.
- Use detection rules to flag anomalies related to T1547.001 and T1053.005.
Service Creation Monitoring
- Monitor for new or suspicious Windows service installations (T1543.003) tied to unauthorized binaries or payloads.
Create and Test Incident Response Plans
- Define clear steps for ransomware detection, containment, communication, and recovery.
- Conduct tabletop exercises simulating ransomware scenarios involving double extortion and data leaks.
Threat Intelligence Integration
- Stay updated on DragonForce’s evolving tactics, Indicators of Compromise (IoCs), and affiliate behaviors through threat intel feeds and security bulletins.
What are the MITRE ATT&CK TTPs of DragonForce Ransomware?
| Tactic | Technique | Observed Methods |
| Initial Access | Trusted Relationship (T1199) | Used pre-installed RMM tools from former hosting to gain domain admin access |
| Exploit Public-Facing Application | Exploited SimpleHelp RMM using CVE‑2024‑57726/27/28 to infect MSP and downstream clients | |
| Phishing (T1566) | Targeted credentials via phishing, MFA push bombing, SIM swap through affiliates like Scattered Spider | |
| Execution | Command & Scripting Interpreter: PowerShell (T1059.001) | Launched malicious tools (“winupdate.exe”) using PowerShell |
| RMM Software Execution | Installed AnyDesk and other RMM tools via service installation | |
| Persistence | Create/Modify System Process: Service (T1543.003) | Maintained persistence by installing AnyDesk and other services |
| Discovery | File & Directory Discovery (T1083) | Used FileSeek to build file inventory lists |
| Active Directory Discovery | Leveraged AD tools like ADFind and network scanners | |
| Credential Access | Credential Dumping | Employed techniques similar to Mimikatz via RMM tools to steal credentials |
| Defense Evasion | BYOVD – Bring Your Own Vulnerable Driver | Used vulnerable drivers to bypass AV/EDR; disabled defenses |
| Clear Windows Event Logs (T1070.001) | Automatically removed event logs post-encryption | |
| Service Impersonation | Leveraged AnyDesk/MSP tools to impersonate admin accounts | |
| Lateral Movement | Exploitation of Remote Services | Used RDP, VPN, and RMM tools to move laterally in environment |
| Active Directory Abuse | Abused AD trust and conducted AD enumeration | |
| Exfiltration | Exfiltration Over SFTP or Custom Tool (T1657) | Transferred data using “winupdate.exe” or SFTP/WebDAV to DLS |
| Impact | Data Encrypted for Impact (T1486) | Used double extortion: encrypted data and threatened leak on leak site |
| Data Leak & Extortion | Operated Dedicated Leak Site (DLS); used cartel messaging tactics to demand payment |
Conclusion
In conclusion, DragonForce Ransomware represents a fast-evolving and dangerous threat in today’s cyber landscape. Its use of leaked tools, advanced evasion techniques, and organized affiliate model makes it highly effective and adaptable. While its links to LockBit remain unclear, its tactics and global reach show a strong understanding of modern ransomware operations. Defenders must stay alert, apply best practices, and update their security measures regularly to protect against this rising threat.
How Can SOCRadar Help?
DragonForce is a growing ransomware group known for aggressive double extortion tactics and targeting a wide range of industries. It uses both custom and borrowed tools to steal data, encrypt systems, and pressure victims into paying ransoms. SOCRadar offers strong, proactive defense tools to detect and stop DragonForce attacks before they cause harm.
Extended Threat Intelligence
SOCRadar tracks DragonForce’s changing Tactics, Techniques, and Procedures (TTPs) in real time. This helps organizations stay ahead of the group’s evolving strategies, such as using leaked builders and exploiting weak points in security.
Vulnerability Intelligence & Risk Prioritization
DragonForce often relies on known vulnerabilities to gain access. SOCRadar identifies and ranks these risks based on current threat activity, helping security teams patch high-priority issues fast and reduce exposure.
SOCRadar Vulnerability Intelligence
External Attack Surface Management
DragonForce targets public-facing systems, including RDP, VPNs, and unpatched web services. SOCRadar’s tools scan and map internet-facing assets, helping companies spot shadow IT and close gaps in their external defenses.
SOCRadar Attack Surface Management
Ransomware Intelligence Dashboard
SOCRadar brings together global ransomware trends in a single dashboard. Teams can track DragonForce’s targets, leaked data, and tools to better understand its behavior and plan effective defense and response strategies.