Major Cyber Attacks in Review: April 2025
April 2025 saw a continued surge in impactful cyber incidents affecting healthcare providers, telecom giants, government contractors, and open-source ecosystems. From large-scale data breaches at Ascension and Yale New Haven Health to the exposure of SIM data at SK Telecom and fresh revelations in the GitHub supply chain compromise, this month underscored how attacker focus remains split between credential theft, misconfigurations, and vulnerable third parties.
While some breaches were rooted in year-old intrusions only recently disclosed – like those affecting VeriSource and LSC – others, including the Oracle incident and Royal Mail leak, show how lingering vendor exposures and legacy systems continue to enable persistent access. Meanwhile, ransomware operations and hacktivist activity kept pressure on global enterprises, with the 4chan breach exposing moderation tools and the Fourlis Group suffering €20M in damages tied to pre-holiday disruptions.
This roundup highlights 10 notable incidents from April 2025 and the patterns behind them, giving defenders a clearer view of how today’s threats unfold across industries and technologies.
Patients Affected in Ascension Healthcare Data Breach
In April 2025, Ascension disclosed that a third-party breachhad exposed the sensitive data of over 114,000 patients in Texas, with additional records compromised in other states. The attack was traced back to December 2024 but wasn’t fully confirmed until January 21, 2025. It stemmed from a vulnerability in software used by a former business partner of Ascension, one of the largest private healthcare systems in the U.S.
The breach compromised personal and health data, including names, contact details, Social Security numbers (SSNs), medical record numbers, diagnosis codes, and insurance information. Notably, 96 individuals in Massachusetts were confirmed to have had both medical and SSN details exposed.
While Ascension did not publicly name the software involved, the timing and details suggest a link to the Clop ransomware group’s exploitation of a zero-day vulnerability in Cleo file transfer software. As a precaution, Ascension offered affected patients two years of free identity protection services, including fraud support and credit monitoring.
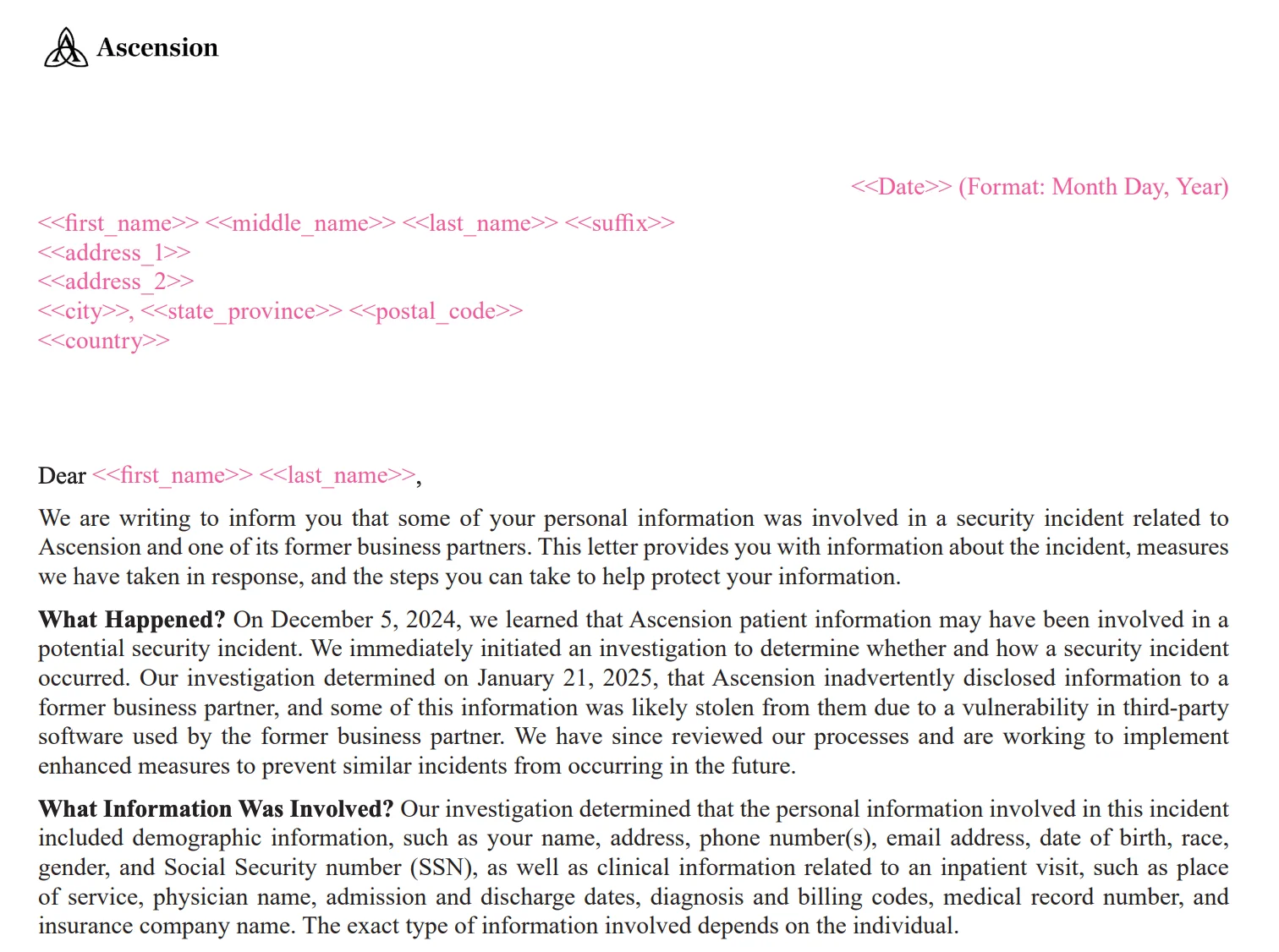
Data breach notification by Ascension (mass.gov)
SK Telecom Breach Exposed SIM Data of 23 Million Customers
SK Telecom, South Korea’s largest mobile carrier, confirmed a major cyber attack that exposed sensitive USIM card data belonging to its entire customer base (reportedly over 23 million users).
Detected on April 19, the breach raised widespread concerns over SIM swapping, a tactic where threat actors use stolen SIM data to hijack phone numbers and intercept communications.
Although no names or financial details were leaked, technical identifiers like IMSI, MSISDN, and authentication keys were compromised. The breach also likely impacted mobile virtual network operator (MVNO) users who rely on SK Telecom’s infrastructure.
To contain the threat, SK Telecom launched an emergency SIM replacement program, offering free replacements to its users. However, limited supply meant only 6 million SIMs could be distributed through May. The carrier also began developing a SIM formatting system for users to update their cards remotely.

The SK Telecom breach exposed the SIM data of 23 million customers.
VeriSource Breach Affected 4 Million Individuals
In April 2025, employee benefits administrator VeriSource disclosed a year-old data breach that impacted 4 million individuals, including employees and dependents of client organizations. Although the intrusion occurred on February 27, 2024, and was discovered the following day, the company only finalized its notification process over a year later, on April 17, 2025.
The breach exposed a range of sensitive personal data, including names, addresses, dates of birth, gender, and Social Security numbers (SSNs). The stolen records were tied to benefit administration services VeriSource provides to corporate clients across the U.S.
While there has been no reported misuse of the compromised data, VeriSource is offering 12 months of free credit monitoring and identity protection services. The company also advised affected individuals to monitor their financial accounts for suspicious activity. The breach notification was filed with the Maine Attorney General’s Office, confirming the scope of the exposure.

Data breach notification by VeriSource (maine.gov)
Yale New Haven Health Data Breach Exposed Over 5.5 Million Patient Records
Yale New Haven Health, Connecticut’s largest healthcare system, confirmed a data breach affecting more than 5.5 million individuals following a cyber attack in March 2025. The attackers gained access to personally identifiable information (PII) and healthcare-related data from patients across the provider’s network.
The stolen data varied by individual and included names, dates of birth, Social Security numbers (SSNs), contact details, race and ethnicity, as well as medical record numbers and patient classification details. Although Yale New Haven has not confirmed the type of attack in its public notice, spokespersons hinted at a highly sophisticated operation, and the scale suggests ransomware or data extortion tactics.
At the time of reporting, no known ransomware group had claimed responsibility.

The Yale New Haven Health Data Breach exposed over 5.5 million patient records.
4chan Hack Exposed Staff Data, Admin Tools, and Source Code
In April 2025, the controversial online forum 4chan was breached by threat actors linked to rival site Soyjak.party, in an attack dubbed “Operation Soyclipse”. The intrusion exposed sensitive staff information, internal admin tools, and portions of the site’s PHP source code.
Attackers claimed the operation had been ongoing for over a year and culminated in the April 14 takedown of 4chan’s infrastructure. Leaked materials included screenshots of moderation tools, source code, ban templates, and internal staff listings, such as the usernames and emails of moderators and “janitors”. The breach also reportedly impacted 4chan Pass subscribers, whose personal data may have been compromised.

4chan breach reveals admin tools and source code. (Image Source)
The compromised admin tools reportedly allowed access to:
- User IP logs and location data
- phpMyAdmin database controls
- Site-wide moderation functions
- Board activity logs and statistics
The source code was posted on Kiwi Farms, sparking concern over potential reuse vulnerabilities. Analysts noted the forum was running a PHP version from 2016, likely missing key security patches.
Post-attack, 4chan experienced outages and degraded performance, with Cloudflare errors and stripped-down site views indicating major infrastructure damage. This breach is among the most serious in 4chan’s history and could risk exposing those behind its controversial boards to retaliation.
IKEA Operator Fourlis Group Lost €20M in Ransomware Attack
In late November 2024, Fourlis Group – the franchise operator for IKEA in Greece, Cyprus, Romania, and Bulgaria – was hit by a ransomware attack that caused an estimated €20 million in damages. The disruption, which unfolded just before Black Friday, severely impacted IKEA’s replenishment and e-commerce operations through February 2025.
Although the attack became public in early December, Fourlis later confirmed that IKEA’s home furnishings segment was the most affected, with €15 million in losses recorded by year-end, and another €5 million spilling into 2025.
Reportedly, no ransom was paid, and system restoration was conducted with external cybersecurity experts. Fourlis Group also claims it fended off multiple follow-up attacks, and a forensic investigation found no evidence of personal data leaks.

IKEA operator was targeted in a ransomware attack. (Image Source)
Data Breach at Lab Testing Provider LSC Affected 1.6 Million Patients
Laboratory Services Cooperative (LSC), a medical testing provider, recently confirmed a significant data breach, which occurred in October 2024 and impacted 1.6 million individuals. The intrusion, detected on October 27, allowed threat actors to access and exfiltrate sensitive files containing patient and employee data.
The stolen data includes a wide range of personally identifiable information (PII) and health records such as:
- Names, birthdates, and Social Security numbers (SSNs)
- Contact details, government IDs, and insurance information
- Medical records, diagnosis/treatment data, and lab results
- Financial data, including banking and payment card details
Notably, the breach also affected Planned Parenthood patients at select centers that used LSC for lab services. For employees, data on dependents and beneficiaries was also compromised.
Although no dark web activity has been linked to the stolen data so far, the full extent of the breach remains unclear, and LSC has not disclosed whether extortion was involved.

Data breach notification by LSC (maine.gov)
GitHub Supply Chain Attack Linked to SpotBugs Project
Researchers at Unit 42 have linked the March 2025 GitHub supply chain attack – which impacted over 200 repositories including Coinbase’s agentkit – to a compromised GitHub Actions workflow in the SpotBugs project.

The GitHub supply chain attack has been traced back to SpotBugs project.
To summarize:
- Initial entry point: Attackers exploited a pull_request_target misconfiguration in spotbugs/sonar-findbugs, triggering a poisoned pipeline execution (PPE).
- Credential theft: A SpotBugs maintainer’s personal access token (PAT) was exfiltrated, providing write access to SpotBugs and Reviewdog repositories.
- Delayed execution: The attackers waited three months before launching the broader campaign in March 2025.
- Account staging: A malicious pull request was submitted via the randolzfow account, which then invited jurkaofavak to push the tampered workflow.
- Payload delivery: Malicious code was injected to print CI/CD secrets directly to workflow logs.
- Downstream impact: The poisoned reviewdog/action-setup@v1 was used by tj-actions/eslint-changed-files, leading to exposure in tj-actions/changed-files and Coinbase’s agentkit. No damage was reported.
This attack chain demonstrates how misconfigured workflows and over-permissioned tokens in open-source CI/CD pipelines can enable long-tail supply chain breaches.
Oracle Confirmed Legacy Server Breach, Prompting CISA Warning
Oracle privately confirmed to customers that threat actors breached a legacy environment, known as Oracle Cloud Classic, exfiltrating old client credentials including usernames, hashed passwords, and email addresses.
The breach reportedly began in January 2025 using a 2020 Java exploit to deploy malware and access Oracle Identity Manager data. The breach was detected in late February.
Initially denying any Oracle Cloud breach, Oracle has since notified affected clients, stating the incident impacted two obsolete servers and not its current cloud infrastructure. However, the attacker, known as “rose87168,” posted records from 2024 and 2025 on BreachForums, casting doubt on Oracle’s framing of the incident.
In response, CISA issued guidance, urging organizations to rotate exposed credentials, eliminate embedded secrets in infrastructure code, and enable phishing-resistant MFA. The agency highlighted the long-term risks of credential exposure, especially when hardcoded into enterprise systems.
For deeper insights, see SOCRadar’s full blog: Everything You Need to Know About Oracle Cloud Security Incident by rose87168.
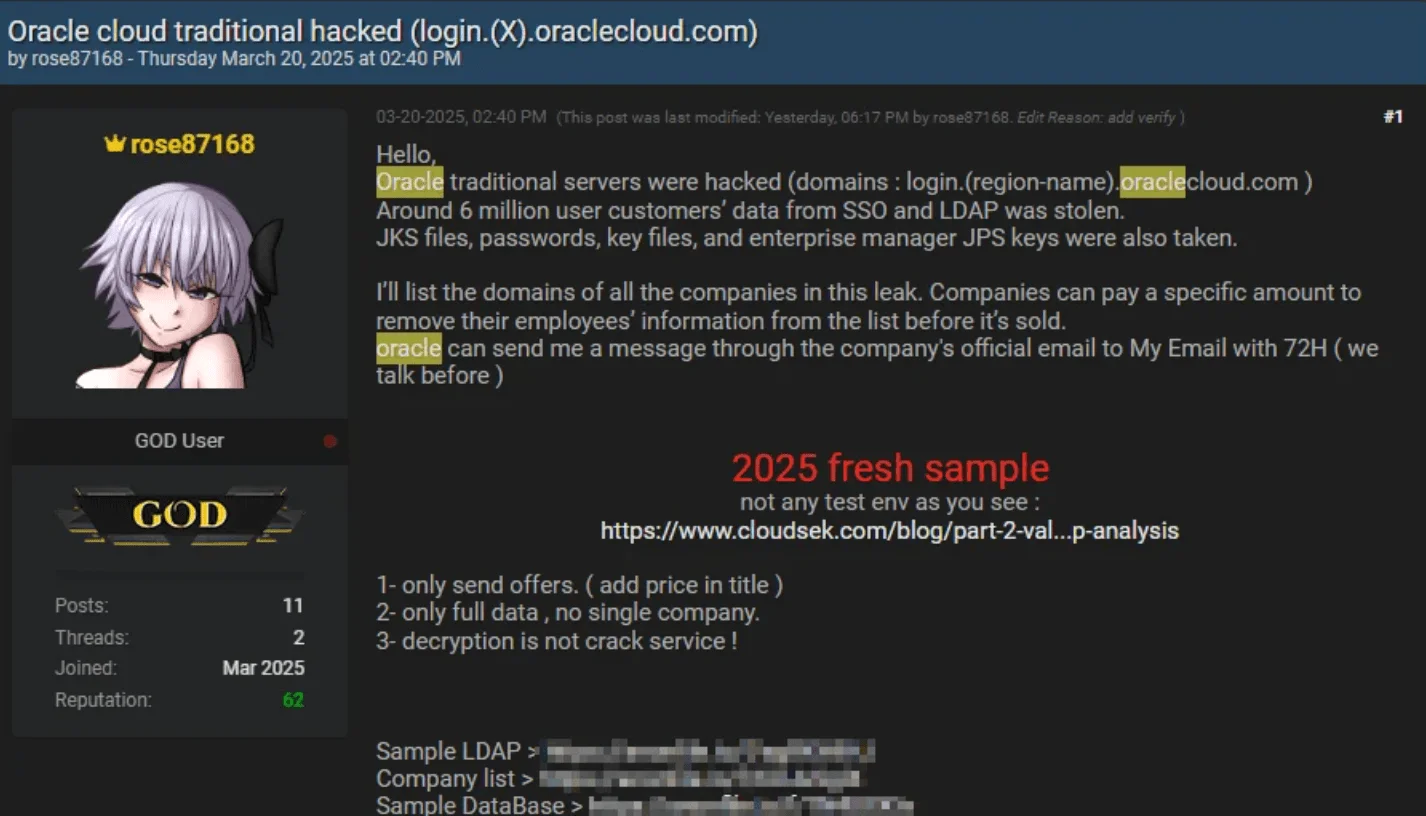
Oracle hack post by rose87168
Royal Mail Group Breach Leaked 144GB of Internal Data
In March 2025, a hacker known as GHNA leaked 144GB of data allegedly stolen from Royal Mail Group, including internal communications, delivery route data, customer PII, and marketing lists. The leak featured Zoom recordings and backend files, much of it linked to Spectos, a third-party analytics vendor.
Royal Mail acknowledged the incident was under investigation with Spectos, though it did not confirm the full scope. GHNA, known for breaching multiple organizations, hinted the attack stemmed from Spectos’ access. The breach follows Royal Mail’s 2023 ransomware hit and underscores ongoing risks in vendor-related exposure.
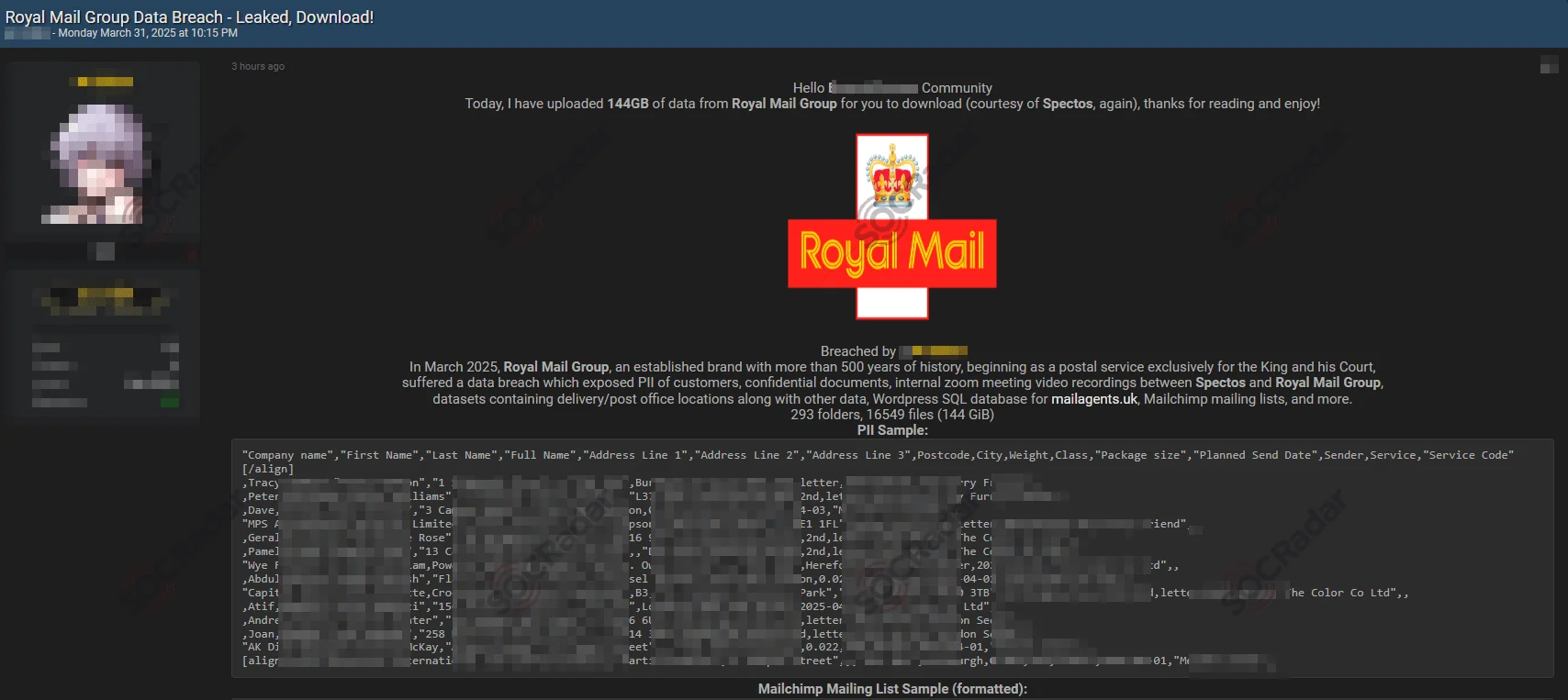
Leak post about the Royal Mail Group data breach (SOCRadar Dark Web News)
How SOCRadar Helps You Detect Exposure and Reduce Risk Early
Security teams need more than isolated tools to stay ahead of emerging threats; they need connected visibility across their digital footprint. SOCRadar brings this together through:
- Real-Time Monitoring of Hidden Web Spaces – Keep tabs on breach forums, leak channels, and darknet activity tied to your brand or data with SOCRadar’s Dark Web Monitoring.
- Enriched Threat Context via the Cyber Threat Intelligence module – Understand not just what’s targeting you, but who and how – through detailed intelligence on actors, exploits, and indicators.
- Asset Discovery – Gain a continuous view of your exposed infrastructure to detect forgotten, misconfigured, or risky digital assets. Check out SOCRadar’s Attack Surface Management (ASM) module.
- Immediate Risk Notifications – Get alerted the moment your credentials, domains, or brand surface in suspicious places with Brand Protection.
SOCRadar’s Attack Surface Management (ASM) module, Digital Footprint
By unifying external threat visibility with actionable insights, SOCRadar empowers organizations to close security gaps before they become incidents.