The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added five security flaws impacting Advantive VeraCore...
Taiwanese company Moxa has released a security update to address a critical security flaw impacting its PT...
Maritime and logistics companies in South and Southeast Asia, the Middle East, and Africa have become the...
Inside the most innocent-looking image, a breathtaking landscape, or a funny meme, something dangerous could be hiding,...
In cybersecurity, confidence is a double-edged sword. Organizations often operate under a false sense of security, believing...
Unpatched TP-Link Archer routers have become the target of a new botnet campaign dubbed Ballista, according to...
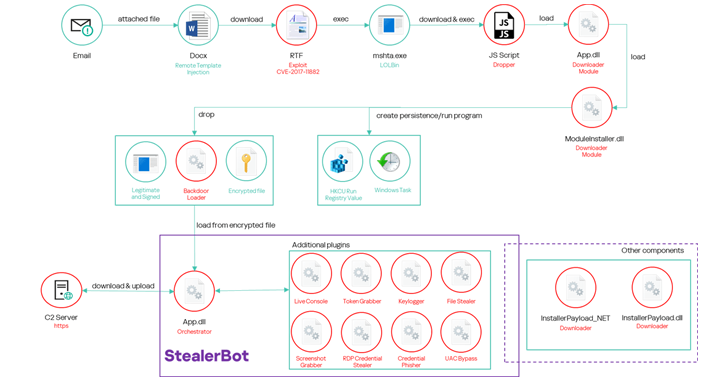
The threat actor known as Blind Eagle has been linked to a series of ongoing campaigns targeting...
Cybercriminals are using AI for help in planning and conducting cyberattacks—but cybersecurity vendors are fighting back. Learn...
Threat intelligence company GreyNoise warns that a critical PHP remote code execution vulnerability that impacts Windows systems...
Microsoft announced that it will drop support for the Remote Desktop app (available via the Microsoft Store)...